Warning: Undefined array key "status" in /www/wwwroot/pcoof.com/git/index.php on line 79
🔗更新日志
🎉 New APatch release 10763 is available 🎉
Changelog Upgrade KernelPatch to 0.10.7 Upgrade java and rust dependences Fix compat syscall, 32-bits su command is supported now Shrink apd size Remove buggy and redundant hide manager feature Re-designed About and Module Screen UI, thanks to SanmerDev MRepo's design Fix os error 2 during installing modules Switch to new enableEdgeToEdge, drop accompanist/systemuicontroller Optimize APatch Safe Mode Fix module online upgrade not working Re-design exclude modifications feature Translation imported, thanks to all translators More optimizations and minor changes
Notes The newly designed exclusion module modifies the logic, and from now on, applications that have already been granted ROOT permissions no longer support exclusion because it does not conform to the logic of normal usage scenarios; By default, modules will no longer be excluded because not all software will check the current environment, which undoubtedly brings unnecessary power consumption and heat to the phone. You can manually configure the applications that need to be excluded. It should be noted that if you are upgrading from a version of KernelPatch below 0.10.7 instead of a completely new installation, you need to manually delete the/data/adb/ap/package_config file and reconfigure it on the SuperUser screen, otherwise a BUG may be occurred. We have noticed that some older devices (mainly those with Linux kernel versions less than 5) may experience unlimited loading of SuperUser Screen, and even some applications may not be able to use ROOT permissions. This is a known issue and is currently under investigation.
👉 Report bug or feature request: https://github.com/bmax121/APatch/issues/new/choose
🔗更新日志
🎉 New APatch release available 🎉
- Upgrade KernelPatch to 0.10.5 (@bmax121)
- Strip busybox so that APatch's size decreased (@sekaiacg)
- New refreshed UI (@pomelohan)
- Introduce theme manager and custom dark mode switch (@pomelohan)
- Switch to stable compose dependence release (@pomelohan)
- Fix settings page not scrollable (@pomelohan)
- Enhanced Image flashing operations (@gitclone-url)
- Optimize InstallScreen experience (@TinyHai)
- Refine dialog component and add an animation to UpdateCard (@TinyHai)
- Enable blur behind compose dialog for Android S+ (@pomelohan)
- Add an alertdialog if failed to auth super key (@pomelohan)
- Refactor Installaction UX&UI (@pomelohan)
- Use lsplugin resopt to optimize apk size (@pomelohan)
- Refine WebUI (@5ec1cff)
- Implement KPM Control Feature (@pomelohan)
- Implement isSafeMode detect (@pomelohan)
- Fix extract kpm infomation from boot error (@bmax121)
- Fix round corner for APModule Info Card (@lightsummer233)
- Fix random build signture (@Admirepowered)
- Adapt Zygisk Next WebUI (@Admirepowered)
- Fix twice try when selecting an invalid boot image (@pomelohan)
- Allow system_server devpts read/write chr_file (@pomelohan @bmax121)
- Fix unable to configure exclude feature for non-root apps (@pomelohan)
- Now SuperKey are no longer plaintext in the process of transmission and storage (@bmax121)
- Fix the logic for processing the "UNCOMPRESSED_IMG" header (@qwerty472123)
- kptools: Skip relocation when trying again (@sekaiacg)
- Fix safemode typo (@18712886438)
- Import translations changes (By all contributors ❤️)
Full Changelog: https://github.com/bmax121/APatch/compare/10570...10657
This version includes many updates. Please backup important data before installation or upgrade. We are pleased that Zygisk Next has added support for APatch. To be compatible with its whitelist function, we have added an "exclude" setting button. It should be noted that if Zygisk Next is not used, it has no practical significance because we have not yet implemented this feature due to time constraints. It is a known issue that some software cannot obtain ROOT permission, but only a very small number of software have experienced this bug. We are doing our best to solve and develop it. Thank you for your support and understanding.
Report bug or feature request: https://github.com/bmax121/APatch/issues/new/choose
🔗更新日志
- fix os error when install module
- fix uninstall androidpatch will lose all root config
Full Changelog: https://github.com/bmax121/APatch/compare/10569...10570
🔗更新日志
- Fix patch error caused by 'find kallsyms_marker error' (For example: OnePlus 12 with kernel 6.1.57+ and etc)
- Try to fix module install os error 22 or 5, but not 100% guaranteed.
Full Changelog: https://github.com/bmax121/APatch/compare/10568...10569
🔗更新日志
- Refactor KernelPatch installation logic and initial support for A/B upgrade after OTA, by @pomelohan and @Admirepowered
- Introduce Module WebUI feature from ksu
- Introduce APatch update notifier
Full Changelog: https://github.com/bmax121/APatch/compare/10533...10568
Warning: Undefined variable $repo in /www/wwwroot/pcoof.com/github/md.php on line 32
Warning: Undefined variable $git in /www/wwwroot/pcoof.com/github/func.php on line 465
Warning: Undefined variable $git in /www/wwwroot/pcoof.com/github/func.php on line 465
Warning: Undefined variable $git in /www/wwwroot/pcoof.com/github/func.php on line 465
Warning: Undefined variable $git in /www/wwwroot/pcoof.com/github/func.php on line 465
Warning: Undefined variable $git in /www/wwwroot/pcoof.com/github/func.php on line 465
Warning: Undefined variable $git in /www/wwwroot/pcoof.com/github/func.php on line 465
Warning: Undefined variable $git in /www/wwwroot/pcoof.com/github/func.php on line 465
Warning: Undefined variable $git in /www/wwwroot/pcoof.com/github/func.php on line 465
The patching of Android kernel and Android system.
- A new kernel-based root solution for Android devices.
- APM: Support for modules similar to Magisk.
- KPM: Support for modules that allow you to inject any code into the kernel (Requires kernel function
inline-hookandsyscall-table-hookenabled). - APatch relies on KernelPatch.
- The APatch UI and the APModule source code have been derived and modified from KernelSU.
Or download the latest APK from the Releases Section.
- Only supports the ARM64 architecture.
- Only supports Android kernel versions 3.18 - 6.1
Support for Samsung devices with security protection: Planned
Kernel configs:
-
CONFIG_KALLSYMS=yandCONFIG_KALLSYMS_ALL=y -
CONFIG_KALLSYMS=yandCONFIG_KALLSYMS_ALL=n: Initial support
The SuperKey has higher privileges than root access.
Weak or compromised keys can lead to unauthorized control of your device.
It is critical to use robust keys and safeguard them from exposure to maintain the security of your device.
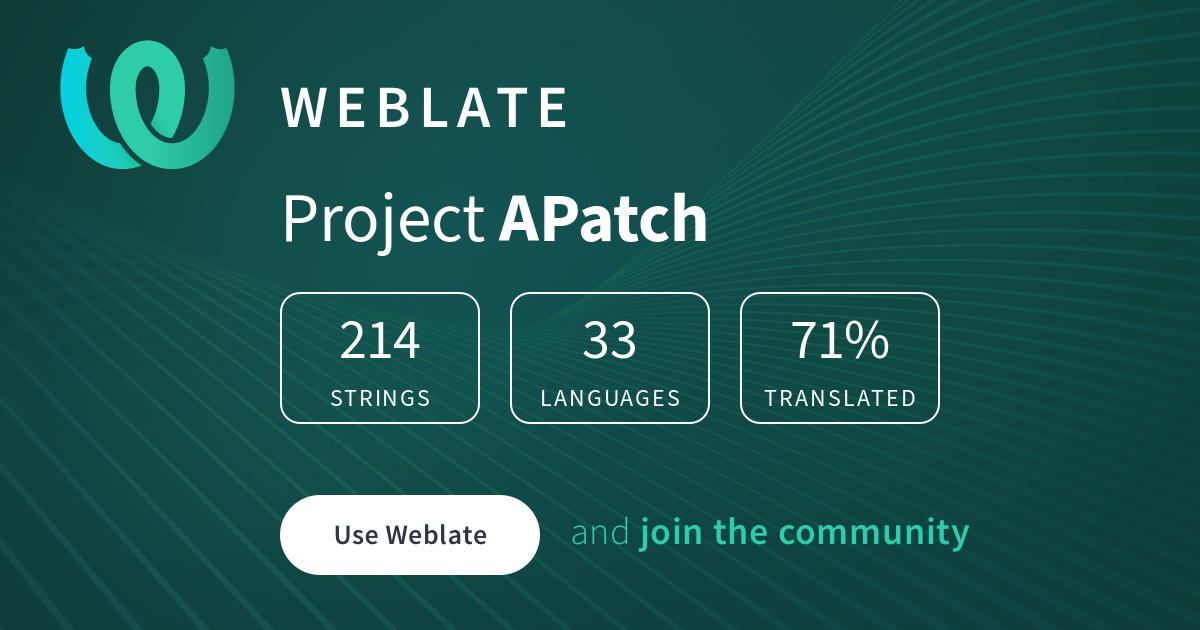
To help translate APatch or improve existing translations, please use Weblate. PR of APatch translation is no longer accepted, because it will conflict with Weblate.
For usage, please refer to our official documentation.
It's worth noting that the documentation is currently not quite complete, and the content may change at any time.
Furthermore, we need more volunteers to contribute to the documentation in other languages.
- Telegram Channel: @APatchUpdates
- Telegram Group: @APatchDiscussions(EN/CN)
- Telegram Group: 中文
- KernelPatch: The core.
- Magisk: magiskboot and magiskpolicy.
- KernelSU: App UI, and Magisk module like support.
APatch is licensed under the GNU General Public License v3 GPL-3.